7. WAPT Server Advanced Configuration¶
The WAPT Server configuration file on GNU/ Linux and macOS systems is found in /opt/wapt/conf/waptserver.ini or in /opt/wapt/waptserver/waptserver.ini.
The WAPT Server configuration file on Windows is found in C:\wapt\conf\waptserver.ini.
Attention
Modification of these files is reserved for advanced users!!
7.1. Default configurations of waptserver file and nginx¶
7.1.1. Modify the [options] section of waptserver.ini¶
Several options can be defined in the [options] section.
[options]
Options (Default Value) |
Description |
Example |
|---|---|---|
|
Defines where the WAPT Agents are stored on the WAPT Server. |
agents_folder = /var/www/wapt/waptagent |
|
Defines whether websocket connections should be authenticated.
If |
allow_unauthenticated_connect = True |
|
Allows the initial registration of the WAPT Agent using a login and password. |
allow_unauthenticated_registration = True |
|
Debug only - Allows unsigned status data from Agent. |
allow_unsigned_status_data = True |
|
Defines a custom WAPT Server application root path. |
application_root = wapt |
|
Enables authentication logs. |
authentication_logs = False |
|
Enables automatic configuration when waptsetup is installed. |
auto_create_waptagent_from_config = True |
|
Defines the host certificate lifetime (in days). |
client_certificate_lifetime = 500 |
|
Defines whether unused :ref:` Windows KB should be automatically deleted <auto_kb_clean>` from the WAPT Server. |
cleanup_kbs = False |
|
Defines the websocket client timeout (in seconds). |
clients_read_timeout = 10 |
|
Defines the host certificate signing certificate. |
clients_signing_certificate = C:\private\org-coder.crt |
|
Defines the host certificate signing CRL periodicity (in days). |
clients_signing_crl_days = 15 |
|
Defines the host certificate signing CRL path. |
clients_signing_crl = C:\private\org-coder.crt |
|
Defines the host certificate signing CRL URL. |
clients_signing_crl_url = https://srvwapt.mydomain.lan/crl |
|
Defines the host certificate signing key path. |
clients_signing_key = C:\private\org-coder.crt |
|
Defines the maximum allowed delay before WAPT Agent requests time out (in seconds). |
client_tasks_timeout = 5 |
|
If x64, allows you to copy all WinPE from |
copy_winpe_x64_in_tftp_folder = True |
|
Defines the maximum allowed delay before PostgreSQL queries time out (in seconds). |
db_connect_timeout = 10 |
|
Defines the url of the PostgreSQL server (by default WAPT use a local Unix Socket). |
db_host = https://wapt.mydomain.lan |
|
Defines the maximum simultaneous connections to the PostgreSQL database. |
db_max_connections = 100 |
|
Defines the PostgreSQL database that the WAPT Server connects to. |
db_name = wapt |
|
Defines the password for authenticating the user on the PostgreSQL database (by default WAPT uses a local UNIX socket). |
db_password = WAPT_DB_PASSWORD |
|
Defines the port of the PostgreSQL server. |
db_port = 5432 |
|
Defines the database stale timeout (in seconds). |
db_stale_timeout = 500 |
|
Defines the PostgreSQL user connecting to the database. |
db_user = wapt |
|
Defines the default acl for a new user opening the WAPT Console. |
default_ldap_users_acls = admin |
|
Automatically downloads the |
download_wsusscn2 = False |
|
Enables WAPT Store Webui (Deprecated). |
enable_store = False |
|
Encrypts host package with client certificate. |
encrypt_host_packages = True |
|
Adds basic authentication to WAPT Server. |
htpasswd_path = True |
|
Defines the proxy server to allow the WAPT Server to recover its CRL. |
http_proxy = http://srvproxy.mydomain.lan:3128 |
|
Adds additional known CA to verify certificates. |
known_certificates_folder = /opt/wapt/ssl/ |
|
Defines the UPN Active directory user for SSO and/or waptserver-ldap mode for self-service. |
ldap_account_service_login = wapt-ldap@ad.tranquil.it |
|
Defines the user password for SSO and/or waptserver-ldap mode for self-service. |
ldap_account_service_password = PASSWORD |
|
Defines the LDAP authentication base DN. |
ldap_auth_base_dn = dc=mydomain,dc=lan |
|
Defines the LDAP authentication server. |
ldap_auth_server = srvads.mydomain.lan |
|
Sets SSL authentication on LDAP connections. |
ldap_auth_ssl_enabled = False |
|
Enables the search of nested group in Active Directory. |
ldap_nesting_group_support = False |
|
Enables the search on Active Directory primary group users. |
ldap_primary_group_ad_support = False |
|
Lists subnets without authentication requirement. |
list_subnet_skip_login_wads = 192.168.0.0/24,192.168.1.0/24 |
|
Enables authentication to use WADS (format is |
login_on_wads = True |
|
Defines the log level. Possible values are: |
loglevel = debug |
|
Sets the maximum simultaneous WAPT client connections. |
max_clients = 2048 |
|
Sets the minimum SuperAdmin password length. |
min_password_length = 15 |
|
Defines the Nginx web server HTTP port (Windows only). |
nginx_http = 8080 |
|
Defines the Nginx web server HTTPS port (Windows only). |
nginx_https = 44380 |
|
If one of the option is set, it will not log it: |
optimized_authentication_logs = False |
|
Défines the periodicity at which the WAPT Server verifies the synchronization status of remote repositories (in minutes). |
remote_repo_update_delay = 5 |
|
Enables websocket communication with WAPT Agents configured as remote repositories. |
remote_repo_websockets = False |
|
Defines the random string for initializing the Python Flask application server. The string is generated when first installing the WAPT Server and is unique for every WAPT Server. |
secret_key = FKjfzjfkF687fjrkeznfkj7678jknk78687 |
|
Defines the WAPT Server UUID (this anonymous id is used for WAPT statistics). |
server_uuid = 76efezfa6-b309-1fez5-92cd-8ea48fc122dc |
|
Defines the maximum allowed time the session is opened (in seconds). |
session_lifetime = 352120 |
|
Defines the maximum allowed time difference for the websockets (in seconds). |
signature_clockskew = 72000 |
|
Defines the authentication token lifetime (in seconds). |
token_lifetime = 43200 |
|
Defines the path to the trusted signers certificate directory. |
trusted_signers_certificates_folder = C:\private\org-coder.crt |
|
Defines the path to trusted users CA certificate directory. |
trusted_users_certificates_folder = C:\private\org-coder.crt |
|
Enables a WAPT Agent to register using its kerberos account.
If |
use_kerberos = True |
|
Enables client certificate authentication. |
use_ssl_client_auth = True |
|
Verifies whether the Active Directory SSL / TLS certificate is valid for LDAP connections. |
verify_cert_ldap = False |
|
Enables the WADS feature and enables wapttftpserver. |
wads_enable = True |
|
Defines the folder on the WAPT Server that stores files related to WADS. |
wads_folder = /var/www/waptwads |
|
Defines the LDAP DN of Active Directory User Group allowed to connect to the WAPT Console. |
wapt_admin_group_dn = CN=waptadmins,OU=groups,DC=ad,DC=mydomain,DC=lan |
|
Defines the sAMAccountName Active Directory User Group(s) allowed to connect to the WAPT Console. The value can be several groups, separated by commas. |
wapt_admin_group = waptadmins, wapttechs |
|
Defines the directory path of the WAPT repository. |
wapt_folder = /var/www/wapt |
|
Defines the path to database that stores the status of running tasks. |
wapt_huey_db = C:\Program Files(x86)\wapt\db\waptservertasks.sqlite |
|
Defines the SuperAdmin password for connecting to the WAPT Console. |
wapt_password = 46642dd2b1dfezfezgfezgadf0ezgeezgezf53d |
|
Defines the WAPT Server python service port. |
waptserver_port = 1313 |
|
Defines the SuperAdmin username in the WAPT Console. |
wapt_user = wapt_admin |
|
Defines the location of WAPT WUA folder. |
waptwua_folder = /var/www/waptwua |
|
Defines the list of WakeOnLAN UDP ports to send magic packets to. |
wol_port = 9, 123, 4000 |
|
Defines how to listen to the WAPT Server service. |
wapt_bind_interface = 127.0.0.1 |
|
Defines the location of jinja template used for WADS ipxe script. |
ipxe_script_jinja_path = /opt/wapt/waptserver/templates/ipxe-autoregister.j2 |
7.1.2. Configuring Nginx¶
The default Nginx configuration is as follows:
# uwsgi upstream server
upstream waptserver {
server unix:///run/waptserver/uwsgi.sock;
}
log_format combined_ssl '$remote_addr $ssl_client_s_dn $ssl_client_verify $remote_user [$time_local] '
'"$request" $status $body_bytes_sent '
'"$http_referer" "$http_user_agent"';
server {
listen 80;
listen [::]:80;
listen 443 ssl;
listen [::]:443 ssl;
server_name srvwapt.mydomain.lan;
server_name 192.168.100.12;
access_log "/var/log/nginx/access.log" combined_ssl;
ssl_certificate "/opt/wapt/waptserver/ssl/cert.pem";
ssl_certificate_key "/opt/wapt/waptserver/ssl/key.pem";
ssl_protocols TLSv1.2;
ssl_dhparam "/etc/ssl/certs/dhparam.pem";
ssl_prefer_server_ciphers on;
ssl_ciphers 'EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH';
ssl_stapling on;
ssl_stapling_verify on;
ssl_session_cache none;
ssl_session_tickets off;
# HSTS (ngx_http_headers_module is required) (63072000 seconds)
add_header Strict-Transport-Security "max-age=63072000" always;
ssl_client_certificate "/opt/wapt/conf/ca-srvwapt.mydomain.lan.crt";
ssl_crl "/opt/wapt/conf/ca-check-clients.crl";
ssl_verify_client optional;
gzip_min_length 1000;
gzip_buffers 4 8k;
gzip_http_version 1.0;
gzip_disable "msie6";
gzip_types text/plain text/css application/json;
gzip_vary on;
index index.html;
server_tokens off;
client_max_body_size 12288m;
client_body_timeout 1800;
large_client_header_buffers 4 16k;
proxy_headers_hash_max_size 1024;
proxy_headers_hash_bucket_size 128;
proxy_request_buffering off;
location ^~ /.well-known/acme-challenge/ {
default_type "text/plain";
root /var/www/html;
}
# sub instances
include "/opt/wapt/conf/wapt.d/*.conf";
location /static {
alias "/opt/wapt/waptserver/static";
}
location /ssl {
alias "/var/www/ssl";
}
# not protected URL
location ~ ^/(wapt/waptsetup.*\.exe|wapt/ping|wapt/waptagent/.*|wapt/waptagent\.exe|wapt/waptdeploy\.exe|wapt/conf\.d/.*\.json)$ {
add_header Cache-Control "store, no-cache, must-revalidate, post-check=0, pre-check=0";
add_header Pragma "no-cache";
root "/var/www";
}
location ~ ^/api/v3/(wads_register_host|set_host_wads_status|baseipxe|get_host_ipxe|get_wads_exe.*|get_wads_config)$ {
proxy_http_version 1.1;
proxy_request_buffering off;
include "/opt/wapt/conf/forward_ssl_auth.conf";
rewrite /(.*) /$1 break;
proxy_pass http://127.0.0.1:8080;
}
# not protected URL
location /wads {
alias "/var/www/wads";
}
location = / {
include "/opt/wapt/conf/forward_ssl_auth.conf";
proxy_pass http://127.0.0.1:8080;
}
# SSL protected URL
location /waptwua {
add_header Cache-Control "store, no-cache, must-revalidate, post-check=0, pre-check=0";
add_header Pragma "no-cache";
include "/opt/wapt/conf/forward_ssl_auth.conf";
include "/opt/wapt/conf/require_ssl_auth.conf";
alias "/var/www/waptwua";
}
# SSL protected URL
location ~ ^/(wapt/.*|wapt-diff-repos/.*|licences\.json|sync\.json)$ {
add_header Cache-Control "store, no-cache, must-revalidate, post-check=0, pre-check=0";
add_header Pragma "no-cache";
include "/opt/wapt/conf/forward_ssl_auth.conf";
include "/opt/wapt/conf/require_ssl_auth.conf";
root "/var/www";
}
location /rules.json {
add_header Cache-Control "store, no-cache, must-revalidate, post-check=0, pre-check=0";
add_header Pragma "no-cache";
include "/opt/wapt/conf/forward_ssl_auth.conf";
root "/var/www";
}
# we don't want to expose our list of computers in case someone scan this folder.
location /wapt-host/Packages {
return 403;
}
location ~ ^/(wapt-host/.*)$ {
log_not_found off;
add_header Cache-Control "store, no-cache, must-revalidate, post-check=0, pre-check=0";
add_header Pragma "no-cache";
include "/opt/wapt/conf/forward_ssl_auth.conf";
include "/opt/wapt/conf/require_ssl_auth.conf";
root "/var/www";
}
location ~ ^/.*_kerberos$ {
proxy_http_version 1.1;
proxy_request_buffering off;
include "/opt/wapt/conf/forward_ssl_auth.conf";
auth_gss on;
auth_gss_format_full on;
auth_gss_keytab /etc/nginx/http-krb5.keytab;
proxy_pass http://127.0.0.1:8080;
}
# we need socketio for these actions.
# they are enabled only locally on the loopback
location ~ ^/api/v3/(update_hosts_sid_table|hosts_sid)$ {
proxy_http_version 1.1;
proxy_request_buffering off;
include "/opt/wapt/conf/forward_ssl_auth.conf";
rewrite /(.*) /$1 break;
proxy_pass http://127.0.0.1:8080;
allow 127.0.0.1;
deny all;
}
# we need socketio for these actions
location ~ ^/api/v3/(update_hosts_sid_table|trigger_host_action|reset_hosts_sid|host_tasks_status|trigger_cancel_task|hosts_delete|launch_sync_on_remotes_repos|broadcast_sync_on_remotes_repo)$ {
proxy_http_version 1.1;
proxy_request_buffering off;
include "/opt/wapt/conf/forward_ssl_auth.conf";
include "/opt/wapt/conf/require_ssl_auth.conf";
rewrite /(.*) /$1 break;
proxy_pass http://127.0.0.1:8080;
}
location /get_websocket_auth_token {
return 404;
}
# these actions are not protected by SSL client side certificate, as we perhaps don't have one at this stage.
# in case uwsgi is enabled, we wat this to still be handled by eventlet waptserver as these endpoints are not cpu intensive but often called
location ~ ^/(ping)$ {
proxy_http_version 1.1;
proxy_request_buffering off;
include "/opt/wapt/conf/forward_ssl_auth.conf";
rewrite /(.*) /$1 break;
proxy_pass http://127.0.0.1:8080;
}
# these actions are not protected by SSL client side certificate, as we perhaps don't have one at this stage.
location ~ ^/(login|api/v3/login|api/v3/logout|api/v3/get_hash_json_content|api/v3/waptagent_version|add_host|api/v3/add_host|api/v3/get_waptagent_exe/.*/waptagent.exe)$ {
proxy_http_version 1.1;
proxy_request_buffering off;
include "/opt/wapt/conf/forward_ssl_auth.conf";
rewrite /(.*) /$1 break;
include /opt/wapt/conf/uwsgi_params;
uwsgi_pass waptserver;
}
location / {
proxy_http_version 1.1;
proxy_request_buffering off;
include "/opt/wapt/conf/forward_ssl_auth.conf";
include "/opt/wapt/conf/require_ssl_auth.conf";
include /opt/wapt/conf/uwsgi_params;
uwsgi_pass waptserver;
}
location /socket.io {
proxy_http_version 1.1;
proxy_request_buffering off;
include "/opt/wapt/conf/forward_ssl_auth.conf";
include "/opt/wapt/conf/require_ssl_auth.conf";
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "Upgrade";
proxy_pass http://127.0.0.1:8080/socket.io;
}
}
7.2. Configuring WAPT Server for large deployments¶
The default operating system, Nginx and PostgreSQL settings are adapted for around 400 WAPT Agents. If you have more than 400 clients it is necessary to modify a few system level parameters along with PostgreSQL database, Nginx web and WAPT Server python server.
In the future, the postconf.sh script might take charge of this configuration depending on the expected number of client computers.
With the following parameters, one WAPT Server should scale up to around 5000 concurrent active clients. You may have more clients in the database if they are not all running at the same time. If you have more than 5000 clients it is recommended to have more than one WAPT Server.
The limit in the number of end point clients is due to the bottleneck in the python code and the PostgreSQL backend. WAPT performance gets better with time and in the future WAPT Server might support a large base on a single host. However the Nginx part scales very well and it can takes full advantage of a 10Gbps connection for high load package deployments.
Note
The parameters to be modified below are linked together and should be modified globally and not individually.
7.2.1. Configuring Nginx¶
OS Type |
File location |
|---|---|
Debian and derivatives |
|
RedHat and derivatives |
|
Windows |
|
In the nginx.conf file, modify the worker_connections parameter.
The value should be around 2.5 times the number of WAPT clients (n connections for websockets and n connections for package downloads and inventory upload + some margin).
events {
worker_connections 4096;
}
Then upgrade the number of filedescriptors in the nginx.conf file:
worker_rlimit_nofile 32768;
Depending on the partitioning of your WAPT Server you might have to be careful with the Nginx temporary file upload directory. Nginx acts as a reverse proxy for the WAPT Server Python engine and its does a caching of packages uploaded when uploading a new package from the Console.
The packages are stored in the /var/lib/nginx/proxy directory.
You have to make sure that the partition hosting this directory is large enough.
You may change this directory location using the following Nginx configuration parameter.
$client_body_temp_path
7.2.2. Configuring the Linux System¶
Increase the number of filedescriptors. The system unit file asks for an increase in the allowed number of filedescriptors (LimitNOFILE=32768). We should have the same thing for Nginx. There are a few limits to modify.
First we modify system wide the number of filedescriptors allowed for Nginx and WAPT.
Create the
/etc/security/limits.d/wapt.conf.
cat > /etc/security/limits.d/wapt.conf <<EOF
wapt hard nofile 32768
wapt soft nofile 32768
www-data hard nofile 32768
www-data soft nofile 32768
EOF
Nginx serves as a reverse proxy and makes quite a lot of connections. Each WAPT client keeps a websocket connection up all the time in order to respond to actions from the WAPT Server.
The Linux kernel has a protection against having too many TCP connections opened at the same time and one may get the SYN flooding on port message in the Nginx log. In order to avoid these messages, it is necessary to modify the two following parameters. It should be around 1.5 times the number of WAPT clients.
cat > /etc/sysctl.d/wapt.conf <<EOF
net.ipv4.tcp_max_syn_backlog=4096
net.core.somaxconn=4096
EOF
sysctl --system
7.2.3. Configuring the PostgreSQL database¶
OS Type |
File location |
|---|---|
Debian and derivatives |
|
RedHat and derivatives |
|
Windows |
|
A higher number of clients need a higher number of connections to the PostgreSQL database.
In the postgresql.conf file, you need to increase the following parameter to approximately 1/4 the number of active WAPT Agents.
max_connections = 1000
In /opt/wapt/conf/waptserver.ini file (for Windows C:\wapt\conf\waptserver.ini), db_max_connections should be equal to PostgreSQL max_connections minus 10 (PostgreSQL needs to keep some connections for its housekeeping stuff).
The max_clients parameter should be set around 1.2 times the number of WAPT Agents:
[options]
...
max_clients = 4096
db_max_connections = 990
7.3. Using the command-lines for repository management¶
7.3.1. wapt-get upload-package¶
The wapt-get upload-package <path to the package> command uploads a package onto the main WAPT repository.
The command wapt-get upload-package C:\waptdev\tis-tightvnc.wapt returns:
Using config file: C:\Users\documentation\AppData\Local\waptconsole\waptconsole.ini
Uploading packages to https://srvwapt.mydomain.lan
Please get login for https://srvwapt.mydomain.lan/api/v3/upload_xxx:admin
Password:
c:\waptdev\tis-tightvnc.wapt[================================] 54316019/54316019 - 00:00:17
OK : 1 Packages uploaded, 0 errors
7.3.2. wapt-get scan-packages¶
Hint
This command applies to Windows repositories ONLY.
The wapt-get scan-packages <directory> command rebuilds a Packages file for a WAPT package repository.
The command wapt-get scan-packages C:waptwaptserverrepositorywapt returns:
Using config file: C:\Program Files (x86)\wapt\wapt-get.ini
Packages filename: C:\wapt\waptserver\repository\wapt
Processed packages:
C:\wapt\waptserver\repository\wapt\tis-firefox.wapt
C:\wapt\waptserver\repository\wapt\tis-tightvnc.wapt
C:\wapt\waptserver\repository\wapt\tis-7zip.wapt
Skipped packages:
7.3.3. wapt-scanpackages¶
Hint
This command applies to Linux repositories ONLY.
The wapt-scanpackages <directory> command rebuilds a Packages file for a WAPT package repository.
The command wapt-scanpackages /var/www/wapt/ returns nothing.
7.3.4. Re-signing packages on the WAPT Server using a command line¶
Use this method if re-signing from the WAPT console method does not complete successfully. These commands are ONLY available for WAPT Servers running Linux.
Warning
Before using this method, ensure that your WAPT Server is safe and not under the control of an unauthorized third party entity.
Copy your
.crtand.pemto/tmp/on the WAPT Server using Winscp or an equivalent tool.It is then possible to re-sign all the packages at once on the WAPT Server with the following commands.
wapt-signpackages -d /var/www/wapt-host -c /tmp/wapt_pub_key.crt -k /tmp/wapt_priv_key.pem -s
wapt-signpackages -d /var/www/wapt -c /tmp/wapt_pub_key.crt -k /tmp/wapt_priv_key.pem -s
wapt-scanpackages /var/www/wapt/
If the error Access violation appears, the reason is that the WAPT package is too voluminous.
Edit the package and check this procedure to transfert a voluminous package.
Danger
Remove the .crt and .pem from /tmp/ on the WAPT Server or the server will become a sensitive asset.
For more available options, please see the command line section.
8. Enhancing the security of your WAPT setup - Server side¶
By default, all WAPT packages are signed with your private key, which already provides a great level of security. However you can further improve the security of WAPT.
To fully secure your WAPT setup; you will want to do the following:
Enable authenticated registration to filter who is authorized to register the device with the WAPT Server.
Enable https certificate verification on the WAPT Agents and the WAPT Console to ensure that the WAPT Agents and the WAPT Console are connecting to the correct WAPT Server.
Configure authentication against Active Directory to allow access to the WAPT Console only to authorized WAPT admins.
Enable Client-Side Certificate Authentication to only allow authenticated devices to access the WAPT Server (Note: it is especially important if you want to expose your WAPT Server to the outside in a DMZ).
If you are using the Enterprise version of WAPT and you operate a large fleet with multiple administrators, you may be interested in knowing how to properly configure and apply the ACLs.
8.1. Configuring the firewall on the WAPT Server¶
WAPT Server firewall configuration is essential and should be the first step towards achieving better security in WAPT.
As WAPT aims to be secure by design, only a minimal set of open ports is needed on the WAPT Server compared to other solutions.
You will find in the following documentation firewall tips to improve WAPT security.
8.1.1. Configuring the firewall for WAPT Server on Debian and derivatives¶
By default on Debian Linux, no firewall rule applies.
Disable ufw and install firewalld instead.
ufw disable
apt update
apt -y install firewalld
Simply apply this firewalld configuration.
systemctl start firewalld
systemctl enable firewalld
firewall-cmd --zone=public --add-port=80/tcp --permanent
firewall-cmd --zone=public --add-port=443/tcp --permanent
systemctl restart firewalld
8.1.2. Configuring the firewall for WAPT Server on RedHat and derivatives¶
Simply apply this firewalld configuration.
systemctl start firewalld
systemctl enable firewalld
firewall-cmd --zone=public --add-port=80/tcp --permanent
firewall-cmd --zone=public --add-port=443/tcp --permanent
systemctl restart firewalld
8.2. Configuring kerberos authentication¶
Note
Without kerberos authentication, you have to either trust initial registration or enter a password for each workstation on initial registration.
For more information, visit the documentation on registering a host with the WAPT Server and signing inventory updates.
The kerberos authentication will be used only when registering the device.
8.2.1. Installing the kerberos components and configuring krb5.conf file¶
apt install krb5-user msktutil libnginx-mod-http-auth-spnego
yum install krb5-workstation msktutil nginx-mod-http-auth-spnego
Note
Registering with kerberos is not available with a WAPT Server running on Windows.
Modify the /etc/krb5.conf file and replace all the content with the following 4 lines replacing MYDOMAIN.LAN with your Active Directory domain name (i.e. <MYDOMAIN.LAN>).
Attention
default_realm value MUST be written with ALL CAPS!!
[libdefaults]
default_realm = MYDOMAIN.LAN
dns_lookup_kdc = true
dns_lookup_realm=false
Retrieving a service keytab. Use the kinit and klist. You can use an Administrator account or any other account with the delegated right to join a computer to the domain in the proper destination container (by default CN=Computers).
In the shell transcript below, commands are in black and returned text is commented in light gray:
sudo kinit administrator
## Password for administrator@MYDOMAIN.LAN:
## Warning: Your password will expire in 277 days on Mon. 17 sept. 2018 10:51:21 CEST
sudo klist
## Ticket cache: FILE:/tmp/krb5cc_0
## Default principal: administrator@MYDOMAIN.LAN
##
## Valid starting Expires Service principal
## 01/12/2017 16:49:31 02/12/2017 02:49:31 krbtgt/MYDOMAIN.LAN@MYDOMAIN.LAN
## renew until 02/12/2017 16:49:27
If the authentication request is successful, you can then create your HTTP Keytab with the msktutil command.
Be sure to modify the <DOMAIN_CONTROLER> string with the name of your domain controller (eg: srvads.mydomain.lan).
sudo msktutil --server DOMAIN_CONTROLER --precreate --host $(hostname) -b cn=computers --service HTTP --description "host account for wapt server" --enctypes 24 -N
sudo msktutil --server DOMAIN_CONTROLER --auto-update --keytab /etc/nginx/http-krb5.keytab --host $(hostname) -N
Attention
Be sure to have properly configured your WAPT Server hostname before running these commands;
In order to double check your hostname, you can run echo $(hostname) and it MUST return the name that will be used by WAPT Agent running on client workstations. If your WAPT server is available from the internet, you should add another servicePrincipalName (SPN) to match with the WAPT public URL. In order to update the keytab file, you must run the 2nd msktutil command every time you add a new SPN.
You can add an auto-update task in crontab. It will frequently change the machine account password in Active Directory so you can pass security audits. Crontab content:
32 23 3 * * root msktutil --auto-update --keytab /etc/nginx/http-krb5.keytab
Apply the proper access rights to the
http-krb5.keytabfile. If you are with RedHat based OS with selinux, please fix rights with restorecon.
sudo chmod 640 /etc/nginx/http-krb5.keytab
sudo chown root:www-data /etc/nginx/http-krb5.keytab
sudo chown root:nginx /etc/nginx/http-krb5.keytab
sudo chmod 640 /etc/nginx/http-krb5.keytab
restorecon -v -R /etc/nginx/http-krb5.keytab
8.2.2. Post-configuring kerberos for the WAPT Server¶
You can now use post-configuration script to configure the WAPT Server to use kerberos.
The post-configuration script will configure Nginx and the WAPT Server to use kerberos authentication.
Hint
This post-configuration script MUST be run as root.
/opt/wapt/waptserver/scripts/postconf.sh --force-https
Kerberos authentication will now be configured.
8.2.3. Special use cases¶
8.2.3.1. My WAPT Server does not have access to a writeable Active Directory¶
Connect to your Active Directory (Not a RODC).
Create a computer account srvwapt.
Add a SPN on the srvwapt$ account.
setspn -A HTTP/srvwapt.mydomain.lan srvwapt
Create a keytab for this WAPT Server.
ktpass -out C:\http-krb5.keytab -princ HTTP/srvwapt.mydomain.lan@MYDOMAIN.LAN rndpass -minpass 64 -crypto all -pType KRB5_NT_PRINCIPAL /mapuser srvwapt$@MYDOMAIN.LAN
Reset SRVWAPT$'s password [y/n]? y
Note
If the address of your WAPT Server is different from your active directory domain, replace HTTP/srvwapt.mydomain.lan@MYDOMAIN.LAN with HTTP/srvwapt.othername.com@MYDOMAIN.LAN.
Transfer this file to
/etc/nginx/(with winscp for example).Apply the proper access rights to the
http-krb5.keytabfile. If you are with RedHat based OS with selinux, please fix rights with restorecon.
sudo chmod 640 /etc/nginx/http-krb5.keytab
sudo chown root:www-data /etc/nginx/http-krb5.keytab
sudo chown root:nginx /etc/nginx/http-krb5.keytab
sudo chmod 640 /etc/nginx/http-krb5.keytab
restorecon -v -R /etc/nginx/http-krb5.keytab
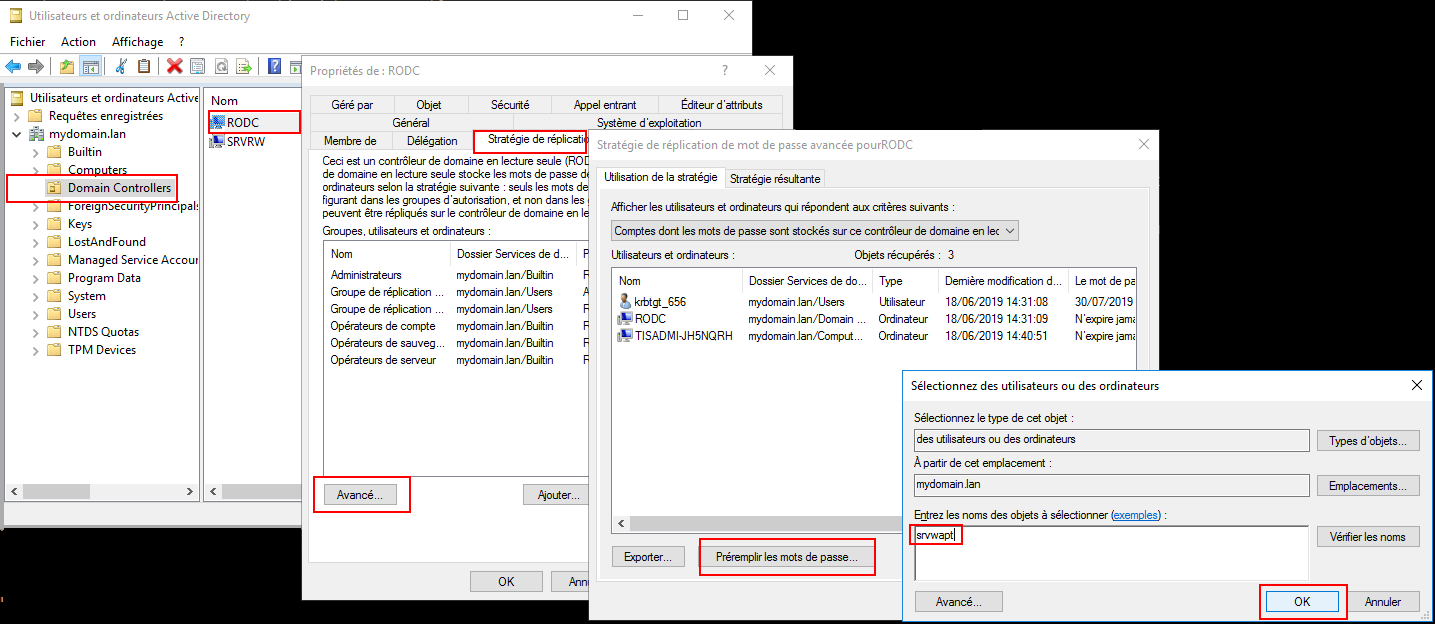
8.2.3.2. WAPT Agents only have access to a RODC domain controller¶
For RODC, add the srvwapt account to the allowed password group for replication.
Remember to preload the password of the WAPT Server with the different RODC servers.
8.2.3.3. You have multiple Active Directory domains with or without relationships¶
If you have multiple Active Directory domains, you MUST create one keytab per domain by following the procedure above, ex:
http-krb5-domain1.local.keytab;http-krb5-domain2.local.keytab;http-krb5-domain3.local.keytab.
You will then have to merge all these keytabs into a unique keytab:
ktutil
read_kt http-krb5-domain1.local.keytab
read_kt http-krb5-domain2.local.keytab
read_kt http-krb5-domain3.local.keytab
write_kt http-krb5.keytab
8.2.4. Debug problems with the kerberos¶
Attention
The WAPT Server address cannot be an IP, Kerberos works well only with DNS.
In your test, the url used MUST be exactly the same address as the one indicated in
C:\Program Files (x86)\wapt\wapt-get.ini.
8.2.4.1. Did you restart nginx correctly?¶
systemctl restart nginx
8.2.4.2. Check the permissions of the http-krb5.keytab file¶
[root@srvwapt.mydomain.lan]# ls -l /etc/nginx/http-krb5.keytab
-rw-r----- 1 root www-data 921 janv. 4 16:20 /etc/nginx/http-krb5.keytab
8.2.4.3. Is kerberos mode active on my WAPT Agent?¶
On the Windows host:
Check in your
C:\Program Files (x86)\wapt\wapt-get.inithat theuse_kerberosvalue isTrue.
[global]
use_kerberos=True
If you change the value, do not forget to restart the WAPT service.
net stop waptservice
net start waptservice
8.2.4.4. Is Kerberos mode active on my WAPT Server?¶
On the Linux host:
Check in your
/opt/wapt/conf/waptserver.inithat theuse_kerberosvalue isTrue.
[options]
use_kerberos=True
Check in your
/etc/nginx/sites-enabled/wapt.confthat this configuration is present.
location ~ ^/.*_kerberos$ {
proxy_http_version 1.1;
proxy_request_buffering off;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
# be sure these headers are not forwarded
proxy_set_header X-Ssl-Client-Dn "";
proxy_set_header X-Ssl-Authenticated "";
auth_gss on;
auth_gss_keytab /etc/nginx/http-krb5.keytab;
proxy_pass http://127.0.0.1:8080;
}
If one of the two configurations is not present, restart the post-configuration and activate kerberos.
8.2.4.5. Checking that the keytab file contains the correct url¶
[root@srvwapt.mydomaine.lan]# KRB5_KTNAME=/etc/nginx/http-krb5.keytab klist -k
Keytab name: FILE:/etc/nginx/http-krb5.keytab
KVNO Principal
---- --------------------------------------------------------------------------
...
3 HTTP/srvwapt.ad.mydomain.lan@AD.MYDOMAIN.LAN
...
8.2.4.6. Trying to register the host using a system account¶
To switch to a system account you MUST use the psexe tool from Microsoft: psexe.
In cmd as an Administrator.
C:\Users\\xxxxxx\\Downloads\\PSTools\\psexec.exe -accepteula -s -i cmd
In the new cmd window, check that you are identified as System.
C:\WINDOWS\\system32>whoami
NT AUTHORITY\System
Run register.
wapt-get register
8.2.4.7. Trying an authentication with the keytab from your WAPT Server¶
On the Linux host.
[root@srvwapt.ad.tranq ~]# ktutil
ktutil: read_kt /etc/nginx/http-krb5.keytab
ktutil: list
slot KVNO Principal
---- ---- ---------------------------------------------------------------------
1 3 srvwapt$@AD.TRANQUIL.IT
2 3 srvwapt$@AD.TRANQUIL.IT
3 3 srvwapt$@AD.TRANQUIL.IT
4 3 SRVWAPT$@AD.TRANQUIL.IT
5 3 SRVWAPT$@AD.TRANQUIL.IT
6 3 SRVWAPT$@AD.TRANQUIL.IT
7 3 host/srvwapt@AD.TRANQUIL.IT
8 3 host/srvwapt@AD.TRANQUIL.IT
9 3 host/srvwapt@AD.TRANQUIL.IT
10 3 HTTP/srvwapt.ad.tranquil.it@AD.TRANQUIL.IT
11 3 HTTP/srvwapt.ad.tranquil.it@AD.TRANQUIL.IT
12 3 HTTP/srvwapt.ad.tranquil.it@AD.TRANQUIL.IT
ktutil: quit
[root@srvwapt.ad.tranq ~]# kinit -k -t /etc/nginx/http-krb5.keytab srvwapt\$@AD.TRANQUIL.IT
[root@srvwapt.ad.tranq ~]# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: srvwapt$@AD.TRANQUIL.IT
Valid starting Expires Service principal
05/02/2021 19:06:05 06/02/2021 05:06:05 krbtgt/AD.TRANQUIL.IT@AD.TRANQUIL.IT
renew until 06/02/2021 19:06:05
8.2.4.8. Verifying that you are successfully obtaining a Kerberos ticket¶
Attention
Always execute commands in system account (see previous point)!
klist purge
klist get http/srvwapt.ad.mydomain.lan
You should get (in your language):
C:\Windows\System32>klist get http/srvwapt.ad.mydomain.lan
LogonId est 0:0x13794d
Un ticket pour http/srvwapt.ad.mydomain.lan a été récupéré.
Tickets mis en cache : (2)
#0> Client : sfonteneau @ AD.MYDOMAIN.LAN
Serveur : krbtgt/AD.MYDOMAIN.LAN @ AD.MYDOMAIN.LAN
Type de chiffrement KerbTicket : AES-256-CTS-HMAC-SHA1-96
Indicateurs de tickets 0x40e00000 -> forwardable renewable initial pre_authent
Heure de démarrage : 2/4/2021 15:51:07 (Local)
Heure de fin : 2/5/2021 1:51:07 (Local)
Heure de renouvellement : 2/11/2021 15:51:07 (Local)
Type de clé de session : AES-256-CTS-HMAC-SHA1-96
Indicateurs de cache : 0x1 -> PRIMARY
KDC appelé : srvads.AD.MYDOMAIN.LAN
#1> Client : sfonteneau @ AD.MYDOMAIN.LAN
Serveur : http/srvwapt.AD.MYDOMAIN.LAN @ AD.MYDOMAIN.LAN
Type de chiffrement KerbTicket : AES-256-CTS-HMAC-SHA1-96
Indicateurs de tickets 0x40a80000 -> forwardable renewable pre_authent 0x80000
Heure de démarrage : 2/4/2021 15:51:07 (Local)
Heure de fin : 2/5/2021 1:51:07 (Local)
Heure de renouvellement : 2/11/2021 15:51:07 (Local)
Type de clé de session : AES-256-CTS-HMAC-SHA1-96
Indicateurs de cache : 0
KDC appelé : srvads.AD.MYDOMAIN.LAN
If that does not work, check in your Active Directory that the serviceprincipalname attribute on the computer account of the WAPT Server has this value: HTTP/srvwapt.mydomain.lan.
8.2.4.9. Check that it works with Firefox¶
Note
You need to first configure Firefox for kerberos authentication.
Type about:config in the URL bar in your Firefox.
Edit
network.negotiate-auth.trusted-uris, and add the url of the WAPT Server:srvwapt.mydomain.lan.You can now visit the url: https://srvwapt.mydomain.lan/add_host_kerberos.
If the authentication does not work, then the WAPT Server will return a 403 error message.
8.2.4.10. In case of an error on one of the previous checks¶
Delete the host account from the Active Directory.
Delete the
/etc/nginx/http-krb5.keytabfile.Reboot the host you are testing with and re-run the keytab creation process again.
Note
It is important to restart the host to purge the kerberos tickets previously obtained by the host.
To avoid restarting you can also execute the command “klist purge” as SYSTEM.
8.3. Activating the verification of the SSL / TLS certificate¶
When running the WAPT Server post-configuration script, the script will generate a self-signed certificate in order to enable HTTPS communications.
The WAPT Agent checks the WAPT HTTPS Server certificate according to the verify_cert value in section [global] in C:\Program Files (x86)\wapt\wapt-get.ini.
Options for |
Working principle of the WAPT Agent |
|---|---|
|
the WAPT Agent will not check the WAPT Server HTTPS certificate. |
|
the WAPT Agent will check the WAPT Server HTTPS certificate using the certificate bundle.
|
|
the WAPT Agent will check the WAPT Server HTTPS certificate with the certificate bundle.
|
Hint
To quickly and easily enable verification of the HTTPS certificate, you can use the Pinning method.
8.3.1. Pinning the certificate¶
The pinning of certificate consists of verifying the SSL/ TLS certificate with a well defined and restricted bundle.
Hint
This method is the easiest when using a self-signed certificate.
For this, you need to launch the following commands in the Windows cmd.exe shell (with elevated privileges if UAC is active).
If you already have a Windows cmd.exe shell open, close it and open a new shell so to take into account the updated environment variables:
wapt-get enable-check-certificate
wapt-get restart-waptservice
Validate the certificate with wapt-get update
When you have executed the update command, make sure that everything has gone well, and if in doubt check Problems when enabling enable-check-certificate.
Attention
If wapt-get enable-check-certificate returns an error, remove the .crt with same name on C:\Program Files (x86)\wapt\sslserver
Note
The command enable-check-certificate downloads the certificate
srvwapt.mydomain.lan.crtin the folderC:\Program Files (x86)\WAPT\ssl\server.It then modifies the file
wapt-get.inito specify the valueverify_cert=C:\Program Files (x86)\wapt\ssl\server\srvwapt.mydomain.lan.crt.The WAPT Agent will now verify certificates using the pinned certificate.
Attention
If you use the certificate pinning method, BE REMINDED to archive the /opt/wapt/waptserver/ssl folder on your WAPT Server.
The file will have to be restored on your WAPT Server if you migrate or upgrade your WAPT Server, if you want the WAPT Agents to continue to be able to establish trusted HTTPS connections with the WAPT Server.
8.3.2. How to use a commercial certificate or certificates provided by your Organization?¶
If the pinning method does not suit you, you can replace the self-signed certificate generated during the installation of WAPT.
Replace the old certificate with the new one in the folder /opt/wapt/waptserver/ssl/ (Linux) or C:\wapt\waptserver\ssl\ (Windows).
The new key pair MUST be in PEM encoded Base64 format.
Note
Special case where your certificate has been signed by an internal Certificate Authority
Certificates issued by an internal Certificate Authority MUST have the complete certificate chain of the Certificate Authority.
You can manually add the certificate chain of the Certificate Authority to the certificate that will be used by Nginx.
Example: echo srvwapt.mydomain.lan.crt ca.crt > cert.pem
For Linux servers it is also necessary to reset the ACLs, if you are with RedHat based OS with selinux, please fix rights with restorecon :
chown root:www-data /opt/wapt/waptserver/ssl/*.pem
chown root:nginx /opt/wapt/waptserver/ssl/*.pem
restorecon -v -R /opt/wapt/waptserver/ssl/
Restart Nginx to take into account the new certificates.
systemctl restart nginx
net stop waptnginx
net start waptnginx
8.3.2.1. Configuring the WAPT Agent¶
For a commercial certificate you can set verify_cert = 1 in wapt-get.ini.
For a certificate issued by an internal Certificate Authority, you MUST place the certificate in the C:\Program Files (x86)\wapt\ssl\server\ca.crt folder and specify the certificate path with verify_cert in the wapt-get.ini file of the WAPT Agent.
To apply the new configuration to your entire fleet:
Regenerate a WAPT Agent with the appropriate settings.
Use a WAPT package to modify
wapt-get.iniand push the certificate.
8.3.3. Verifying the certificate in the WAPT Console¶
When the WAPT Console first starts, it reads the content of C:\Program Files (x86)\WAPT\wapt-get.ini and it builds its configuration file C:\Users\admin\AppData\Local\waptconsole\waptconsole.ini.
This properly sets the verify_cert attribute for the HTTPS communication between the WAPT Console and the WAPT Server.
8.4. Configuring user authentication against Active Directory  ¶
¶
By default, the WAPT Server is configured with a single SuperAdmin account whose password is setup during initial post-configuration.
On large and security-minded networks, the SuperAdmin account should not be used since it cannot provide the necessary traceability for administrative actions that are done on the network assets.
It is thus necessary to configure authentication against the Active Directory for the WAPT Console users; this will allow to use named accounts for tasks.
Note
Active Directory authentication is used to authenticate access to the inventory via the WAPT Console.
However, all actions on the WAPT equipped remote devices are based on X.509 signatures, so an Administrator will need both an Active Directory login AND a private key whose certificate is recognized by the remote devices that the Administrator manages using WAPT.
Only the SuperAdmin account and the members of the Active Directory security group waptadmins will be allowed to upload packages on the main repository (authentication mode by login and password).
8.4.1. Enabling Active Directory authentication¶
To enable authentication of the WAPT Server with Active Directory, configure the file
waptserver.inias follows.
Note
The WAPT Server configuration file on GNU/ Linux and macOS systems is found in /opt/wapt/conf/waptserver.ini or in /opt/wapt/waptserver/waptserver.ini.
The WAPT Server configuration file on Windows systems is found in C:\wapt\conf\waptserver.ini.
#waptserver.ini
wapt_admin_group=waptadmins
ldap_auth_server=srvads.mydomain.lan
ldap_auth_base_dn=DC=mydomain,DC=lan
ldap_auth_ssl_enabled=False
Options (Default Value) |
Description |
Example |
|---|---|---|
|
LDAP DN of Active Directory User Group allowed to connect to WAPT Console. |
wapt_admin_group_dn = CN=waptadmins,OU=groups,DC=ad,DC=mydomain,DC=lan |
|
Defines the sAMAccountName of the Active Directory User Group allowed to connect to WAPT Console, it is a list that can contain several groups.
You can use this option over |
wapt_admin_group = waptadmins, wapttech |
|
Defines the LDAP authentication server. |
ldap_auth_server = srvads.mydomain.lan |
|
Defines the LDAP authentication base DN. |
ldap_auth_base_dn = dc=domain,dc=lan |
|
Sets SSL authentication on LDAP connections. |
|
|
Checks the SSL certificate for LDAP connections, unless |
verify_cert_ldap = False |
Restart waptserver service.
Warning
For Microsoft Active Directory, Microsoft has announced that SimpleBind* authentication on MS-AD without SSL/TLS will be blocked by default from April 2020. If you do not have a certificate installed, you will have to modify a registry key to have authentication working.
Note
By default Samba-AD does not allow SimpleBind authentication without SSL/TLS.
If you do not have a valid certificate you will need to modify the ldap server require strong auth parameter in /etc/samba/smb.conf.
For more information you may refer to Tranquil IT’s documentation on Samba-AD.
8.4.2. Enabling Single Sign On (SSO) for the WAPT Console and the self-service¶
Warning
This configuration is only available for WAPT Servers running on WAPT supported Linux distributions.
You can use Kerberos to authenticate yourself on the waptconsole and the selfservice. This way, users do not need to enter their password.
It is not necessary to register the WAPT Agent using kerberos in order to use the kerberos SSO on the WAPT Console and in the Self-Service.
8.4.2.1. Preparing the WAPT Server for Kerberos Single Sign On¶
Attention
To enable Kerberos on the WAPT Server with use_kerberos = True option, launch the WAPT Server postconf script.
/opt/wapt/waptserver/scripts/postconf.sh
Please, refer to the documentation on configuring kerberos for authentication beforehand.
If you do not want to use Kerberos for Client registration, set the option allow_unauthenticated_registration to True.
Finally, restart the waptserver and wapttasks services.
systemctl restart waptserver wapttasks
There are 3 ways to configure the WAPT Server for Kerberos and LDAP authentication.
For each of these methods, you will need to modify the waptserver.ini.
The first way is the least secure.
This method does not verify the LDAP certificate nor does it use a secured port to contact the WAPT Server.
ldap_auth_ssl_enabled = False
verify_cert_ldap = False
Indeed, ldap_auth_ssl_enabled = False will not try to query the Active Directory using the LDAPS protocol.
The verify_cert_ldap = False option is set if you do not use SSL/TLS support.
Hint
If your Active Directory Server is a Samba-AD and you have this option in the waptserver.ini, then the Samba-AD server will refuse the connection.
ldap_auth_ssl_enabled = False
By default Samba-AD does not allow SimpleBind authentication without SSL / TLS.
If you do not have a valid certificate you will need to modify the ldap server require strong auth parameter in /etc/samba/smb.conf.
For more information you may refer to Tranquil IT documentation on Samba-AD.
The second method is more secure but still not perfect.
The method enables SSL authentication without verifying the certificate.
ldap_auth_ssl_enabled = True
verify_cert_ldap = False
The WAPT Server will try to use by default the LDAPS protocol without verifying the certificate when contacting the Active Directory.
The third and recommanded way is the most secure.
ldap_auth_ssl_enabled = True
verify_cert_ldap = True
To make the method work, you will have to enable the SSL/TLS support.
Then, you will need to add these options in the
waptserver.ini:ldap_account_service_login = wapt-ldap@ad.tranquil.it ldap_account_service_password = PASSWORD ldap_auth_server = srvads.mydomain.lan ldap_auth_base_dn = dc=mydomain,dc=lan use_kerberos = True
The
ldap_account_service_loginandldap_account_service_passwordrequire a service user account on your Active Directory.It is not necessary that the service account had elevated right, just enough rights to read groups and group members. In other words, the WAPT Server MUST have read rights on the
memberofattribute in the Active Directory.Finally, restart services on the WAPT Server:
systemctl restart waptserver wapttasks
8.4.2.2. Configuring the WAPT Agent¶
On the client side, you will have to make sure that theses 2 options are set in the wapt-get.ini of the WAPT Agent:
service_auth_type = waptserver-ldap
use_kerberos = True
It is possible to make changes in wapt-get.ini manually or by deploying a WAPT package with the new configuration settings.
An example package is available from the Tranquil IT repository.
With this configuration, you can launch your WAPT Console or your selfservice without being prompted for a password.
To make this feature work, the Active Directory has to be available.
Note
The WAPT Console will continue to ask for a login / password. It is perfectly normal, this way you can use another user than the current user logged in the underlying desktop session.
Otherwise, you just have to put your login and click on OK.
8.4.3. Enabling SSL/ TLS support for the LDAP connection to the Active Directory Domain Controller¶
By default, authentication on Active Directory relies on LDAP SSL (default port 636).
SSL / TLS is not enabled by default on Microsoft Active Directory until a SSL certificate has been configured for the Domain Controller.
Note
The WAPT Server uses Certificate Authority bundles from the operating system for validating the SSL/ TLS connection to Active Directory.
If the Active Directory certificate is self-signed or the certificate has been signed by an internal CA, you will need to add the certificates to the operating system certificate store.
To do so, just add a Certificate Authority in the /etc/pki/ca-trust/source/anchors/ and update the certificate store.
cp cainterne.crt /usr/local/share/ca-certificates/cainterne.crt
update-ca-certificates
cp cainterne.crt /etc/pki/ca-trust/source/anchors/cainterne.crt
update-ca-trust
certutil -addstore -f "ROOT" cainterne.crt
Once you have setup LDAP SSL/ TLS on your Active Directory (please refer to Microsoft documentation for that), then you can enable support for SSL/TLS security for AD in
waptserver.ini.
ldap_auth_ssl_enabled = True
Restart waptserver service.
8.5. Configuring Client-Side Certificate Authentication  ¶
¶
If your business needs a public WAPT Server on Internet, it can be secured with Client-Side Certificate Authentication.
That configuration restricts the visibility of the WAPT Server only to registered WAPT clients. It is done by relying on the WAPT Agent private key generated during registration. It works as follows:
The WAPT Agent sends a CSR to the WAPT Server which the WAPT Server signs and sends back to WAPT Agent.
Using the signed certificate, the Agent can access protected parts of the Nginx web server.
Note
We strongly recommend enabling Kerberos or login / password registration in the WAPT Server post-configuration.
Warning
All actions are to be carried out on the WAPT Server
8.5.1. Enabling Client-Side Certificate Authentication on WAPT Server¶
Warning
For Linux check if the symbolic link in sites-enabled exists:
cd /etc/nginx/sites-enabled/
find . -maxdepth 1 -type l -ls
The expected result should be:
269091 0 lrwxrwxrwx 1 root root 36 juil. 22 15:51 ./wapt.conf -> /etc/nginx/sites-available/wapt.conf
Otherwise use the following command:
ln -s /etc/nginx/sites-available/wapt.conf ./wapt.conf
To enable the authentication, you need to add those parameters on WAPT server configuration file in the option section:
use_ssl_client_auth = True
Relaunch the post-configuring script.
Attention
Please note that as of 2024-10-28, WAPT does not support CRL, which means that when you delete a host in the WAPT Console, the host will still have access to the WAPT repository.
The WAPT Deployment utility cannot use https to retrieve the WAPT Agent, you will have to add this section in the file:
server {
listen 80;
listen [::]:80;
server_name _;
location ~ ^/(wapt/waptsetup-tis.exe|wapt/waptagent.exe|wapt/waptdeploy.exe)$ {
add_header Cache-Control "store, no-cache, must-revalidate, post-check=0, pre-check=0";
add_header Pragma "no-cache";
root "/var/www";
}
return 301 https://$host$request_uri;
}