Using WAPT Windows Update Agent (WAPTWUA)  ¶
¶
Hint
WAPT is able to manage Windows Updates on your endpoints and replace automatic Windows Updates or a WSUS Server.
Note
WAPTWUA works with the WUA Windows API.
For more information: https://docs.microsoft.com/en-us/windows/win32/wua_sdk/using-the-windows-update-agent-api.
Attention
WAPTWUA can not operate concurrently with the Windows store.
Working principle¶
Video demonstration:
Each Patch Tuesday, the WAPT Server downloads an updated wsusscn2.cab file from official Microsoft servers.
By default, downloads are scheduled once a day and no download is triggered if the wsusscn2.cab file has not changed since the last download.
Hint
In order to make WAPTWUA work, The WAPT Server must have access to:
windowsupdate.microsoft.com
..windowsupdate.microsoft.com
..update.microsoft.com
windowsupdate.com
download.windowsupdate.com
download.microsoft.com
download.windowsupdate.com
wustat.windows.com
ntservicepack.microsoft.com
go.microsoft.com
dl.delivery.mp.microsoft.com
Even though you may choose other sources for Windows updates, ports 443 and 80 need to accept incoming trafic on the WAPT Server.
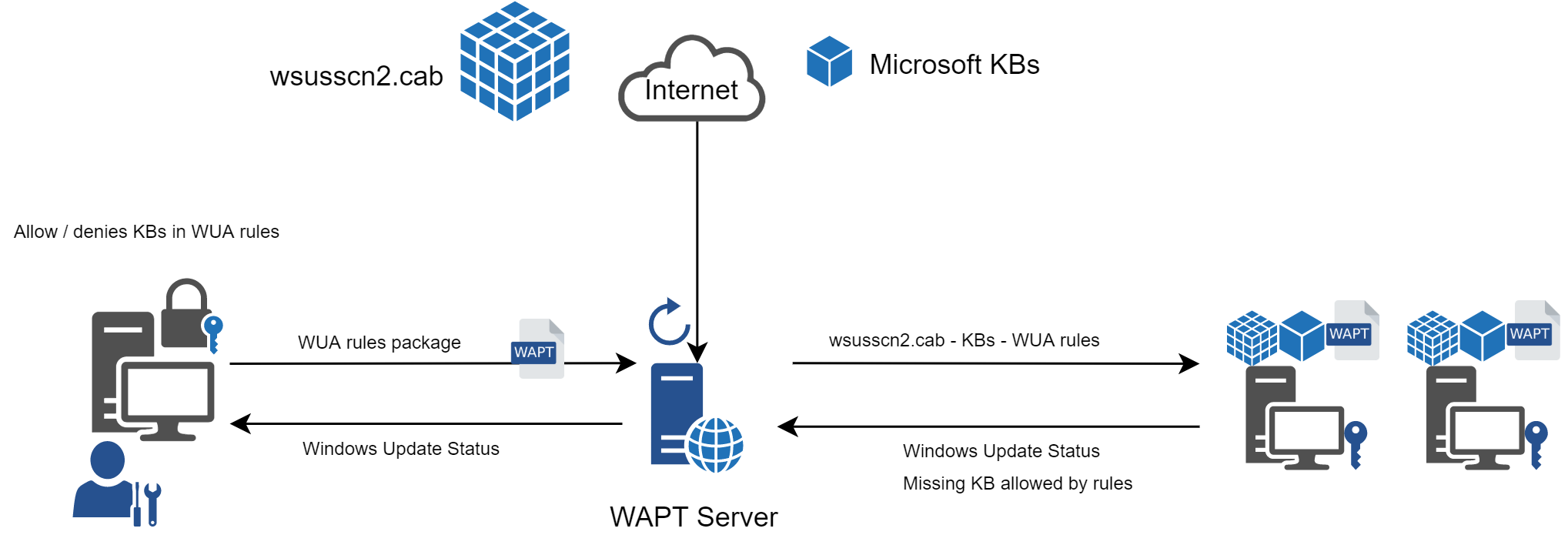
Flow diagram of the WAPT Windows Updates¶
The wsusscn2.cab file is then downloaded by the WAPT Agent from the WAPT Server repository and then passed on to WUA Windows utility to crunch the update tree for the host.
Regularly, the host will analyze the available updates using the wsusscn2.cab file and send its list of needed updates to the WAPT Server.
If an update is pending on the host and if that update is not present on the WAPT Server, the WAPT Server will download the needed update from official Microsoft servers.
Hint
This mode of operation allows WAPT to download only the necessary updates on the computers, thus saving bandwidth, download time and disk space.
Note
On the WAPT Server, downloaded updates are stored:
on Linux hosts in
/var/www/waptwua;on Windows hosts in
C:\wapt\waptserver\repository\waptwua.
The WAPT Windows Update Agent repository download URL is based on the repo_url parameter in wapt-get.ini:
Note
If repository replication is used, it will synchronize WAPT Windows Update out of the box. For this, the
waptwuafolder needs to be included in the folder to synchronize.
If a proxy is required to access Internet, then be sure to set the proxy server in the waptserver.ini file.
Differences between WAPT Windows Updates and WSUS¶
WSUS downloads by default the updates for selected categories. This can lead to a very large update database and lots of storage.
WAPT Windows Update only downloads updates that have been requested by at least one client computer. This helps to keep the local database small (a few 10s of Gigabytes) and it can be easily cleaned up if you want to recover space.
Major OS upgrades¶
Major OS upgrades are upgrades from one OS version to another. That includes, for example, upgrades from Windows 7 to Windows 10, or from Windows 10 1903 to Windows 10 20H2.
Major version upgrades are not handled in the same way as minor OS upgrades. Major upgrades are handled via the downloading of the new install ISO content (same content as for a fresh install) and running the setup.exe with the correct parameters. This process is the same for WSUS, SCCM and WAPT Windows Updates.
In the case of WAPT Windows Updates, you need to create a OS update package using a template package provided on https://store.wapt.fr.
Driver upgrades¶
Driver upgrades via WSUS are not recommended since it is hard to properly handle side effects.
In the case of WAPT Windows Updates, DRIVERS ARE NOT DOWNLOADED since they are not referenced in the wsusscn2.cab files provided by Microsoft.
It is recommended to push driver updates via a custom WAPT package.
If the driver patch is packaged as a .msu, you may package it as a standard WAPT package.
Just select the .msu file and click in the WAPT Console to launch the wizard for simplified package creation.
If the driver update is packaged as a .zip containing the .exe file, you can create a WAPT package containing the necessary files and setup.exe binary with the correct silent flag.
Out of band KB¶
Microsoft sometimes provides OOB updates that are not contained in the wsusscn2.cab index.
Those updates are not included in the main update because they may fix a very specific problem or may have drawbacks in some situations.
If you want to deploy an OOB KB update, you can download it from the Microsoft catalog.
Just select the .msu file and click in the WAPT Console to launch the wizard to create a simple package.
To do so, follow this documentation on packaging .msu files for these Out-of-band updates.
Attention
You have to be careful that OOB updates may break your system, be sure to read the prerequisites on the Microsoft bulletin corresponding to the update and thoroughly test the update.
Configuring WAPTWUA on the WAPT Agent¶
WAPTWUA is configured in wapt-get.ini in [waptwua] section.
You then have several options:
Options (Default Value) |
Description |
Example |
|---|---|---|
|
Enables or disables WAPTWUA on this host. |
enabled = True |
|
Defines whether updates are downloaded directly from Microsoft servers. |
direct_download = True |
|
Defines whether missing update are authorized by default. |
default_allow = True |
|
Defines the Windows Update scan recurrence (Will not do anything if waptwua package rule or |
download_scheduling = 1d |
|
Defines the Windows Update install recurrence (Will do nothing if no update is pending). |
install_scheduling = 2h |
|
Defines whether updates are triggered on host shutting down. |
install_at_shutdown = True |
|
Defines a deferred installation delay before publication in the repository. |
install_delay = 15d |
|
Defines a severity list that will be automatically accepted during a WAPT windows update scan. ex: Important, Critical, Moderate. |
allowed_severities = Important |
|
Defines whether the Windows Update agent will show both the latest KB and the superseeded ones (True), or only the lastest KB (False). |
include_potentially_superseded_updates = True |
Hint
These options can be set when generating the WAPT Agent.
Example [waptwua] section in wapt-get.ini file:
[waptwua]
enabled = True
default_allow = False
direct_download = False
download_scheduling = 7d
install_at_shutdown = True
install_scheduling = 12h
install_delay = 3d
When creating the waptagent.exe from the WAPT Console, these options are equivalent to this:
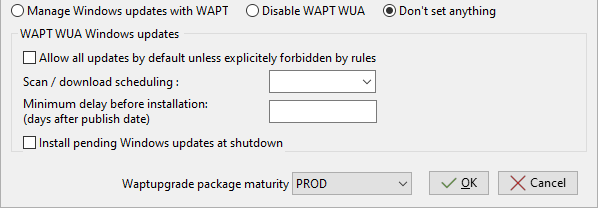
Menu options for the WAPT Windows Update Agent¶
Example source code to modify [waptwua] settings with a WAPT package:
def install():
inifile_writestring(WAPT.config_filename,'waptwua','enabled','true')
inifile_writestring(WAPT.config_filename,'waptwua','install_at_shutdown','true')
inifile_writestring(WAPT.config_filename,'waptwua','download_scheduling','7d')
inifile_writestring(WAPT.config_filename,'waptwua','allowed_severities','Critical,Important')
print('Reload WAPT configuration')
WAPT.reload_config_if_updated()
Using WAPTWUA from the WAPT Console¶
The WAPTWUA is managed with two tabs in the WAPT Console.
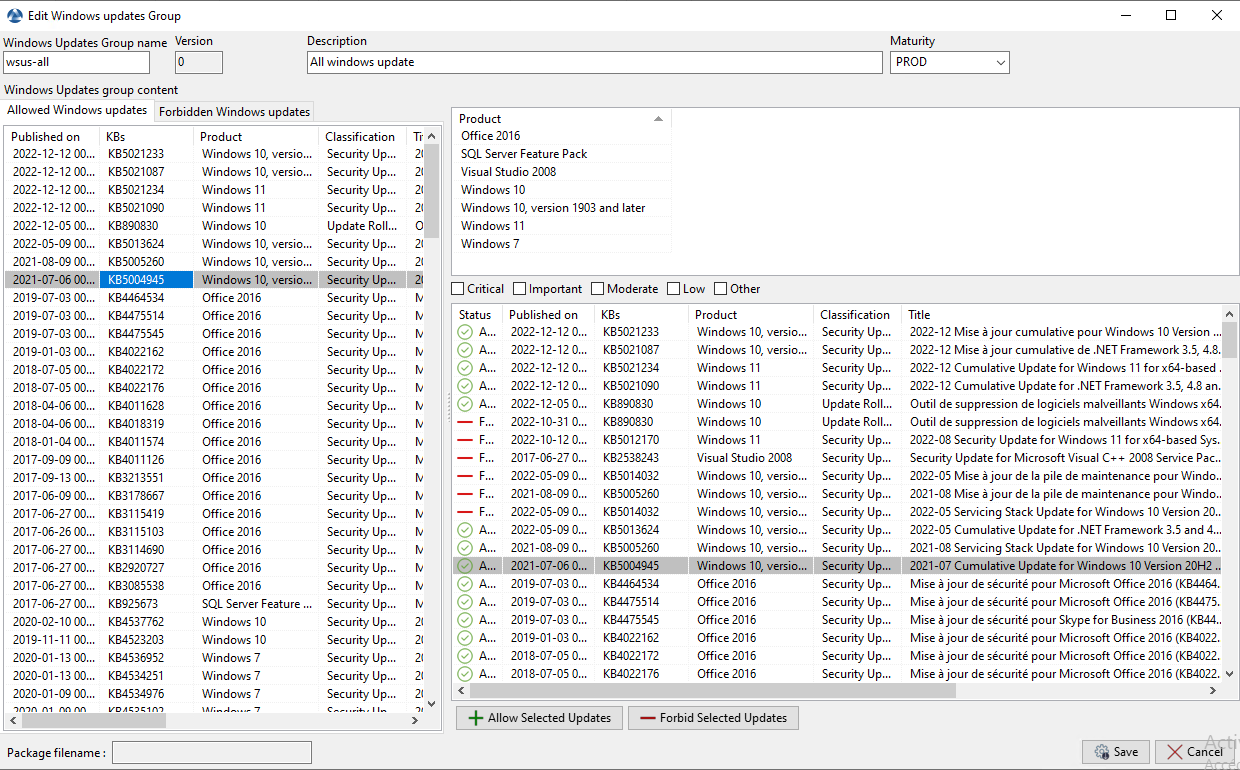
Creating a waptwua package in the WAPT Console¶
The WUA Rules tab allows you to create waptwua rule packages.
When a waptwua package is installed on a host, it indicates to the WAPTWUA Agent what are the authorized or forbidden KBs.
When several waptwua packages are installed on a host, the different rules will be merged.
When a
cabis neither mentioned as authorized, nor mentioned as prohibited, WAPT Agents will then take the value ofdefault_allowinwapt-get.ini.
Note
If the WAPTWUA Agent configuration is set to
default_allow=True, then it will be necessary to specify the forbiddencab.If the WAPTWUA Agent configuration is set to
default_allow=False, then it will be necessary to specify the authorizedcab.
Hint
To test updates on a small set of computers, you can set WAPTWUA default maturity to
PREPROD.You can then test the Windows Updates on a small sample of
PREPRODhosts and if everything is good, you can release the updates to the entire fleet of computers.
Windows Updates tab in the WAPT Console¶
The Windows Update tab lists all needed Windows Updates.
Important
The WAPT Server does not scan the wsussc2.cab itself, it lets the Windows Update Agent utility present on all Windows hosts do it.
If an update seems to be missing from the list, you MUST run a scan on one of the hosts present in the WAPT Console.
If you run a WAPT WUA scan on a Windows 10 client, the CAB and Windows 10 files will be displayed on the Windows Update tab.
The left pane displays update categories, allowing you to filter by:
criticality;
product;
classification.
In the right panel grid, if the Downloaded on column is empty, it means that the update has not yet been downloaded by the WAPT Server and is not present on the WAPT Server (This update is not missing on any host).
To force download an update, do .
To force download the
wsusscn2.cabfile, click on the Download WSUSScan cab from Microsoft Web Site button.To see the Windows Updates downloaded on the WAPT Server, click on the Show download task button.
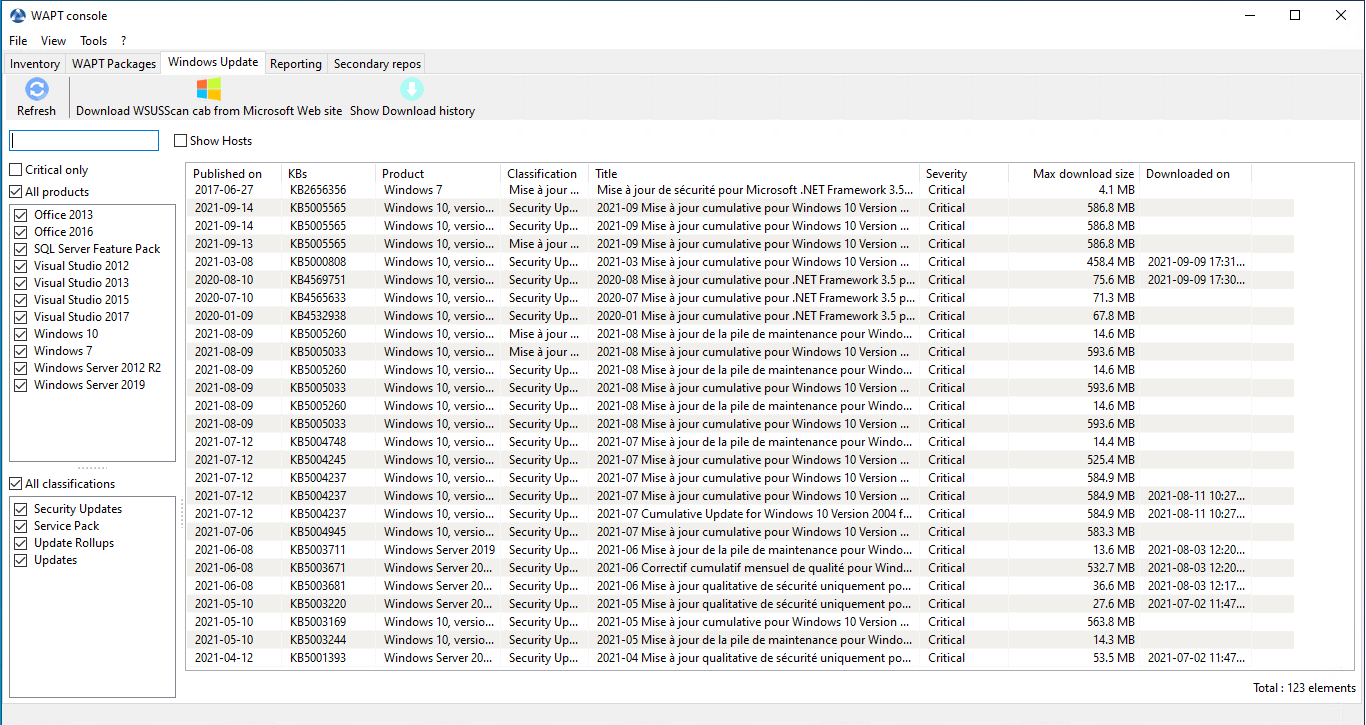
Listing of Windows Updates in the WAPT Console¶
Hint
Every 30 minutes, the WAPT Server will look for updates that have been requested at least once by WAPT Clients and that have not yet been downloaded and cached. If a Windows update has been requested by a WAPT Client and the requested Windows Update is not cached, the WAPT Server will download it from official Microsoft servers.
You can force this scan with the Download index and missing cabs from Microsoft Web site button in the tab
Cleaning old Windows updates¶
You can run the cleanup either manually or automatically.
If the KB is not installed on the host, it is automatically deleted on the WAPT Server between 2:30 am and 3:30 am every day.
It is possible to disable the automatic deletion of KB with the cleanup_kbs option in the waptserver.ini configuration file of the WAPT Server.
Add this setting on the WAPT Server configuration file:
cleanup_kbs = False
To cleanup the waptwua folder, go to the Windows update tab and click on the Delete Unused KB button.
Pressing the button will delete all useless KB stored on the WAPT Server.
It is possible to delete manually from the WAPT Server any Windows Update file that is no longer required.
The WAPT Server will only re-download deleted updates if any of the WAPT Agents requests it.
On the WAPT Server, downloaded updates are stored:
On Linux hosts in
/var/www/waptwua.On Windows hosts in
C:\wapt\waptserver\repository\waptwua.
Launching WUA on clients¶
From the WAPT Console you have three options.
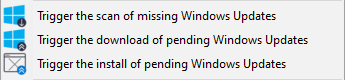
The Trigger the scan of pending Windows Updates button will launch the scan on the client and list all updates flagged for the OS.
The Trigger the download of pending Windows Updates button will launch the downloading of pending updates on the client.
The Trigger the install of pending Windows Updates button will launch the install of downloaded updates on the client.
Hint
When pending updates stored in cache need to be installed, the WAPT Agent triggers the WUA service.
The WAPT Agent will then enable and start the WUA Service temporarily to install the updates. When updates are installed, the WAPT service will stop and disable the WUA service until the next cycle.
State of Windows Update on the host¶
Windows updates can have 4 states on a host.
Status |
Description |
|---|---|
OK |
A Windows update has installed correctly. |
MISSING |
A Windows update has not yet been downloaded to the WAPT Server. |
PENDING |
The WAPT Server knows it has to download an update from official Microsoft servers. |
DISCARDED |
A Windows update was forbidden by rules. |
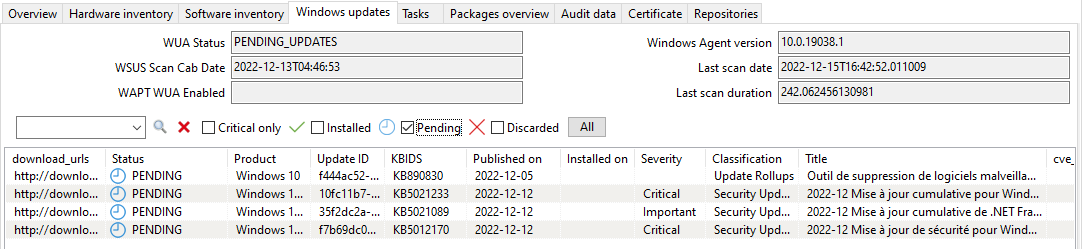
Pending Windows Updates showing in the WAPT Console¶
Notion of UpdateID¶
In WAPT we do not use kbids but instead we use updateids.
This allows us to be finer in the management of updates.
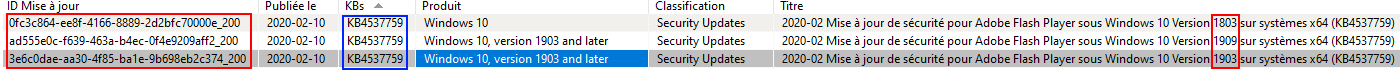
List showing duplicate KB in the WAPT Console¶
In this example, KB4537759 appears multiple times because there are 3 different updateids:
win10 1803;
win10 1903;
win10 1909;
You should therefore authorize updateids and not KB ids.
WAPT does not force Windows to uninstall a Windows Update¶
Attention
Uninstalling a Windows update can be dangerous for the host.
When an update is detected as forbidden by WAPT, its removal will NOT be forced.
If you really want to uninstall an update, you should package the KB that you want to uninstall as a standard WAPT package.
Here is an example:
from setuphelpers import *
uninstallkey = []
def install():
with EnsureWUAServRunning():
run('wusa /uninstall /KB:4023057')