Configuring Kerberos authentication¶
Note
without Kerberos authentication, you have to either trust initial registration or enter a password for each workstation on initial registration;
for more information, visit the documentation on registering a machine with the WAPT Server and signing inventory updates;
the Kerberos authentication will be used only when registering the device;
Installing the Kerberos components and configuring krb5.conf file¶
#Debian
apt install krb5-user msktutil libnginx-mod-http-auth-spnego
#CentOS
yum install krb5-workstation msktutil nginx-mod-http-auth-spnego
Note
The feature is not available with a WAPT Windows server
Modify the /etc/krb5.conf file and replace all the content with the
following 4 lines replacing MYDOMAIN.LAN with your Active Directory
domain name (i.e. <MYDOMAIN.LAN>).
Attention
default_realm must be written with ALL CAPS!!
[libdefaults]
default_realm = MYDOMAIN.LAN
dns_lookup_kdc = true
dns_lookup_realm=false
Retrieving a service keytab. Use the :command:`kinit and klist. You can use an Administrator account or any other account with the delegated right to join a computer to the domain in the proper destination container (by default CN=Computers).
In the shell transcript below, commands are in black and returned text is commented in light gray:
sudo kinit administrator
## Password for administrator@MYDOMAIN.LAN:
## Warning: Your password will expire in 277 days on lun. 17 sept. 2018 10:51:21 CEST
sudo klist
## Ticket cache: FILE:/tmp/krb5cc_0
## Default principal: administrator@MYDOMAIN.LAN
##
## Valid starting Expires Service principal
## 01/12/2017 16:49:31 02/12/2017 02:49:31 krbtgt/MYDOMAIN.LAN@MYDOMAIN.LAN
## renew until 02/12/2017 16:49:27
If the authentication request is successful, you can then create your HTTP Keytab with the msktutil command.
Be sure to modify the <DOMAIN_CONTROLER> string with the name of your domain controller (eg: srvads.mydomain.lan).
sudo msktutil --server DOMAIN_CONTROLER --precreate --host $(hostname) -b cn=computers --service HTTP --description "host account for wapt server" --enctypes 24 -N
sudo msktutil --server DOMAIN_CONTROLER --auto-update --keytab /etc/nginx/http-krb5.keytab --host $(hostname) -N
Attention
Be sure to have properly configured your WAPT Server hostname before running these commands;
In order to double check your hostname, you can run echo $(hostname)
and it must return the name that will be used by WAPT agent running
on client workstations.
apply the proper access rights to the
http-krb5.keytabfile:#Debian sudo chmod 640 /etc/nginx/http-krb5.keytab sudo chown root:www-data /etc/nginx/http-krb5.keytab #CentOS sudo chown root:nginx /etc/nginx/http-krb5.keytab sudo chmod 640 /etc/nginx/http-krb5.keytab
Post-configuring¶
You can now use post-configuration script to configure the WAPT Server to use Kerberos.
The post-configuration script will configure Nginx and the WAPT Server to use Kerberos authentication.
Hint
This post-configuration script must be run as root.
/opt/wapt/waptserver/scripts/postconf.sh --force-https
Kerberos authentication will now be configured.
Special use cases¶
My WAPT server does not have access to a writeable Active Directory¶
connect to your Active Directory (Not a RODC);
create a computer account srvwapt;
add a SPN on the srvwapt$ account;
setspn -A HTTP/srvwapt.mydomain.lan srvwapt
create a keytab for this WAPT server:
ktpass -out C:\http-krb5.keytab -princ HTTP/srvwapt.mydomain.lan@MYDOMAIN.LAN rndpass -minpass 64 -crypto all -pType KRB5_NT_PRINCIPAL /mapuser srvwapt$@MYDOMAIN.LAN Reset SRVWAPT$'s password [y/n]? y
Note
If the address of your WAPT server is different from your active directory domain, replace HTTP/srvwapt.mydomain.lan@MYDOMAIN.LAN with HTTP/srvwapt.othername.com@MYDOMAIN.LAN.
transfer this file to
/etc/nginx/(with winscp for example);apply the proper access rights to the
http-krb5.keytabfile:#Debian sudo chmod 640 /etc/nginx/http-krb5.keytab sudo chown root:www-data /etc/nginx/http-krb5.keytab #CentOS sudo chown root:nginx /etc/nginx/http-krb5.keytab sudo chmod 640 /etc/nginx/http-krb5.keytab
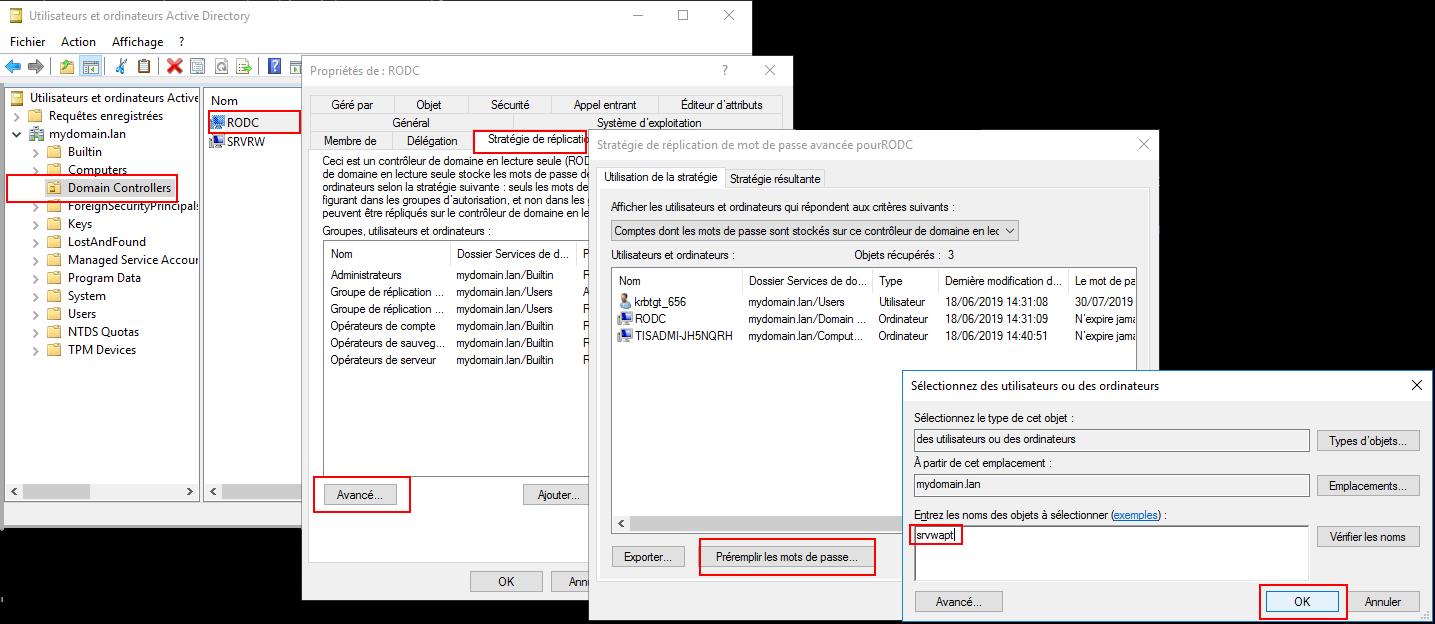
WAPT agent only have access to a RODC domain controller¶
for RODC, add the srvwapt account to the allowed password group for replication;
remember to preload the password of the WAPT server with the different RODC servers;
You have multiple Active Directory domains with or without relationship¶
If you have multiple Active Directory domains,
you must create one keytab per domain by following the procedure
above, ex:
http-krb5-domain1.local.keytab;http-krb5-domain2.local.keytab;http-krb5-domain3.local.keytab;
You will then have to merge all these keytabs
into a unique keytab:
ktutil
read_kt http-krb5-domain1.local.keytab
read_kt http-krb5-domain2.local.keytab
read_kt http-krb5-domain3.local.keytab
write_kt http-krb5.keytab